The New Dimension of Phishing Attacks - Browser in the Browser (BiTB) on the Rise
Phishing attacks have evolved significantly over the years, adapting to new technologies and user behaviors to exploit vulnerabilities more effectively. Even though BiTB was first introduced in 2022 by a security researcher known as Mr.d0x, it’s now becoming a more popular phishing attempt in the current world.
So what actually is a Browser in the Browser (BiTB) Phishing Attack?
As the name goes, it leverages a replication of a browser window inside the website, meaning a fake popup designed as the browser window.
If one is guessing, they might have guessed it right. The main attack vector is the SSO / OAuth functionality. As more & more websites are adapting OAuth login functionalities, the attack area for this phishing method is also on the rise.

How Frequent Is It On the Internet Currently?
There are a lot of companies providing SSO services, taking the name of Google, X (formerly Twitter), Facebook in the general section to steam being popular in the gaming community.
Most of the phishing attacks are done as an aftermath of an initial breach which helps gain trust of the related targets of that specific taken over asset.
Recently, a person named Heron on X (Twitter), received a message from one of his friends asking him to vote for his friends on a random website which needed login to vote. There was a sign in with the Steam button which he clicked and popped up with this.

As OAuth is believed to be a safe way to register on websites using a 3rd Party SSO, it wasn’t something to be doubted initially. Even if you look at the popup it looks legit, at least to me.
But the attacker mainly texted him quoting a name that his friend really doesn’t call him with, which made him think again. He contacted his friend through another source and found out that his discord account was taken over & not to login anywhere.
So he got alerted & didn’t get caught in that trap. But how was he sure that it was a phishing attempt when the domain name in the child window looks genuine? Let us get back to it later about how you can detect this.
Isn’t It Hard to Make Up Something Like This Using JS or CSS?
Not really, Mr.D0x has a collection of these already made, categorized for Chrome both on Windows & Mac including both Dark & Light Mode in this github repository.

The repository in general provides dummy details.

This is the demo of the popup of Chrome Dark in MacOS. We can easily change the HTML CSS inside to change the details.

We need to change the written parts from here to reflect in that popup. It is quite easy when you know a little bit of HTML, CSS & easier when you have ChatGPT.
ChatGPT was used to clone the design of the Google OAuth window.

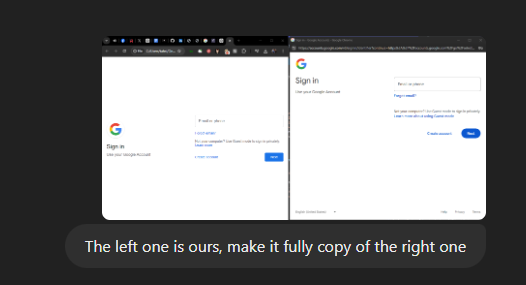

If you have a look at these, in the first glimpse it is quite difficult to identify. Tuning the CSS to match the exact font & weight will make it indistinguishable by looks.
How Can You Actually Be Sure Then Which One Is a Phishing One & Which One Is Not?
If someone encounters something like this, one thing they can do is drag the window and see how it reacts.
If it’s a fake window:
1. It won’t go over the url bar.
2. It will move with the parent window.
3. It won’t go to the back of the parent window in focus.
You can watch this for a clear video of detection. The vector in the video is more developed by design & very hard to detect otherwise.
In conclusion, as phishing attacks grow increasingly sophisticated, incorporating methods like the Browser in the Browser (BiTB) technique which is also likely easier to be developed in this generation of AI, it's imperative for both individuals and organizations to stay ahead of these threats. Regularly educating users on recognizing phishing attempts, implementing robust security protocols, and utilizing multi-factor authentication are critical steps in mitigating risk.





.jpg)