Blogs
Cybersecurity Blog
Stay ahead with insights from Red Sentry’s team, covering penetration testing, compliance, and offensive security trends.


COMPLIANCE
SaaS Security Risks 2026: Misconfigurations, Compliance Gaps, and Data Breach Prevention
Misconfigurations, shadow IT, and over-privileged identities drive 2026 SaaS breaches. To mitigate risks, organizations must adopt continuous, identity-centric governance and automate compliance monitoring.
Dec 16, 2025


COMPLIANCE
Google Dorks Exposed: Protect Your Sensitive Data from Search Engine Reconnaissance
Attackers use Google Dorks to locate exposed sensitive data; therefore, organizations must treat search engines as attack surfaces and implement continuous monitoring to prevent breaches driven by automated reconnaissance.
Dec 12, 2025


EMERGING THREATS
Mitigating CVE-2025-55182: React2Shell Exploits in Modern Web Applications
React2Shell (CVE-2025-55182) is a critical, pre-authentication RCE in React Server Components actively exploited for malware. Immediate patching and WAF defenses are required to prevent data theft and compromise.
Dec 10, 2025

EMERGING THREATS
Securing db_password in .env Files: How to Move to Proper Secrets Management in 2026
Storing db_password in .env files creates security risks like leaks and malware attacks. Organizations must migrate to centralized, encrypted secrets management platforms to ensure compliance.
Dec 9, 2025

PRESS RELEASE
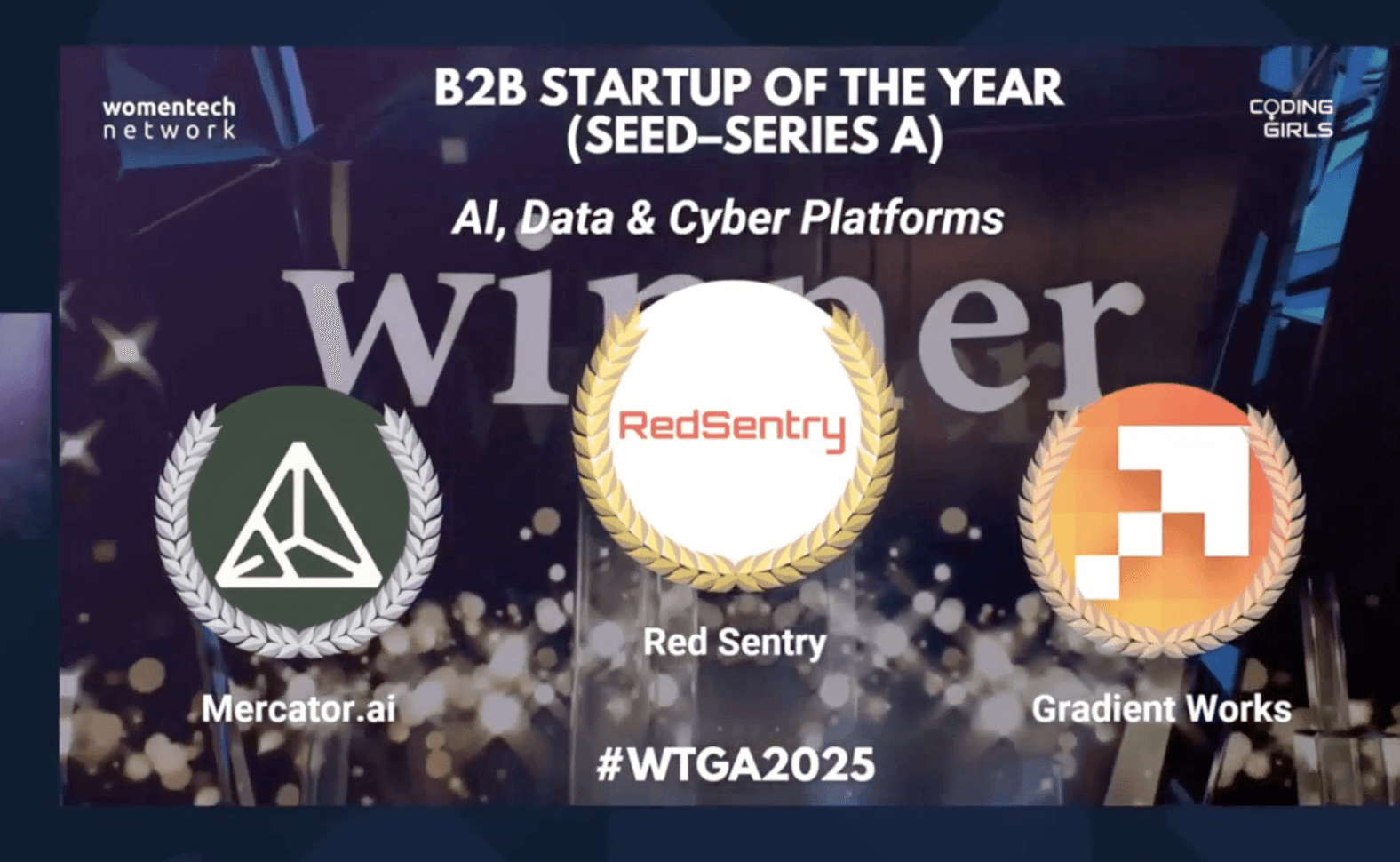
Red Sentry winner at the Women in Tech Global Awards 2025
WomenTech Network announced the 2025 Global Awards winners, honoring 1,760 contestants globally for leadership, innovation, and diversity.
Dec 8, 2025


INDUSTRY
IT Security vs Cybersecurity: Which Does Your Business Need First in 2026?
Differentiates infrastructure-focused IT security from threat-centric cybersecurity. It recommends stabilizing IT basics while prioritizing high-impact cyber controls and compliance through specialized partnerships.
Dec 5, 2025